Understanding about Operating System Hardening and Security Heath Check
In Operating System hardening is a process to ensure vulnerabilities are closed properly which certifies that the Operating System being prevented from attackers.
In infrastructure multiple components has been integrated to provide services each and every layers has to be implement security setting with different metric ( As provided by service provider which has been agreed by customer as well ) . Here we are going to talk about Operating System hardening. If we break down the Operating System hardening it has multiple layers i.e. user settings and file permissions etc..
What would happen if you haven’t implement hardening?
Take an example of your personal workstation account login pass word is guessable; I am sure no one wish to do that. The same way once you do hardening you cannot keep any dictionary words as a pass word for your system that would be implement in globally ( It means this has been applicable to all the user existing in operating system )
Hardening Process
Operating system hardening would be varies depends up on organization and IT security standard whatever they follows. Before implementing we should consider the system is internet facing or non- internet facing based on that hardening and health process would varies.
The major part is that validating the operating system access which ensures that whoever have the login they been in a right access group. If any deviation that can be corrected through implementing the access validation process etc … Consider the second case whereas user existing in system but without right information ( GECOS – normally contains about employee country , full name , OS or application or database ). For overcome and keep the access control in place we do implement sudo … In health check perspective sudo template needs to be validated and provide the right access to users and file sets supposed to be update on regular basis.
Vulnerability Assessment in this we scan all the ports which is listening take an example through http along with some weak algorithm hackers can enter the system , due to which we inspect system by doing Vulnerability Assessment.
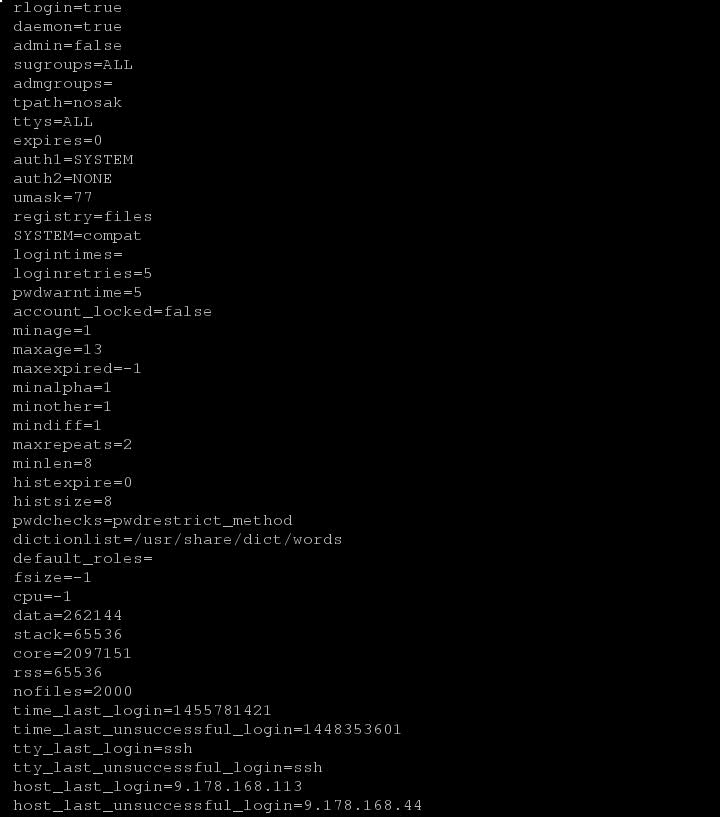
Health check process and documents would have the provided template to OS administrator it’s there responsibility to implement those I am sure that would be a lengthy process (normally Operating System admins never like to do). You could see the below attached screen shot where there are lot many attributes also when you run lsuser command with root privilege you can see the command output given below.
 Next one file permission removal unwanted file access permissions revoked along with proper brainstorming with application/database teams.
Next one file permission removal unwanted file access permissions revoked along with proper brainstorming with application/database teams.
As like multiple process and steps involves in OS hardening and health check process and we can see the same along with practical examples on further documents.
